Quishing Uncovered: A Comprehensive Guide to QR Code Phishing and Quishing Security
Discover how to combat quishing and safeguard your organization from advanced QR code phishing attacks.

Introduction
The role of QR codes has evolved from a simple tool for information sharing to a critical component in our increasingly digital lives. With 1.5 billion people globally embracing QR codes for transactions, the emergence of QR code phishing or quishing – a blend of 'QR Code' and 'Phishing' – represents a significant and growing cyber threat. This whitepaper delves into the alarming rise of Quishing, a phenomenon where 22% of phishing attacks in 2023 involved QR codes, marking a new frontier in cybercrime.
The convenience of QR codes, a staple in our post-pandemic world, has been exploited by cybercriminals through sophisticated QR phishing attacks. These attacks not only compromise devices but also jeopardize sensitive financial data. From an elderly woman in Singapore losing $20,000 overnight to sophisticated scams in the UK and the US, the threat is real and escalating. With each firm facing over 1,200 attacks per week and a 7% increase in global cyber attacks in early 2023, the urgency to address QR code security is paramount.
This whitepaper serves as an essential guide for businesses, cybersecurity professionals, and individuals wanting to enhance awareness and foster robust security practices. As we navigate into 2024, understanding and mitigating the risks associated with QR codes is necessary and a responsibility for all digital citizens.
Understanding Quishing - The Emergence of QR Code Phishing
In this section, we explore the mechanics of this modern cyber threat, shedding light on how seemingly innocuous QR codes can become potent tools for cybercriminals.
Defining QR Phishing - Quishing : A Modern Cyber Threat
Quishing represents a sophisticated form of phishing that leverages QR codes as a tool for deception. This technique diverges from traditional phishing, which predominantly uses misleading emails. Quishing capitalizes on the QR code's capacity to store a wealth of data compactly, leading users to malicious websites, triggering malware downloads, or tricking them into revealing sensitive personal or financial information. This section delves into the mechanics of Quishing, shedding light on how these seemingly harmless codes can become pivotal tools in the wrong hands.
The Evolutionary Path of QR Code Phishing
Initially developed in the 1990s for tracking components in the automotive industry, QR codes have since evolved significantly.Their integration into consumer technology, especially with the widespread adoption of smartphones, has seen a dramatic increase. This rise in popularity, however, has not gone unnoticed by cybercriminals. The exploitation of QR codes for malicious purposes has given rise to the phenomenon of Quishing.
The Growing Relevance of QR Code Phishing Security
As QR codes become more embedded in our daily digital interactions, the importance of understanding and mitigating the risks associated with them escalates. By examining the trajectory of QR code usage and its exploitation by cybercriminals, we aim to equip readers with the knowledge to recognize and protect against these modern phishing tactics. The section will conclude with an emphasis on the critical need for robust QR code phishing security measures in the face of evolving digital threats.
How Quishing Works: Anatomy of a QR Code Phishing Attack
Quishing attacks, while seemingly straightforward, are intricately crafted to exploit the unsuspecting nature of digital users. This section aims to unravel the anatomy of a typical Quishing attack, providing a detailed walkthrough of the entire process from inception to execution. Understanding the mechanics of these attacks is crucial for individuals and organizations to identify and neutralize such threats effectively.
1. Crafting the Deceptive QR Code
The genesis of a Quishing attack lies in creating a fraudulent QR code. Cybercriminals design these codes to mimic legitimate ones, often used in advertising, payment systems, or information sharing. The malicious QR code, however, is embedded with a link that directs the user to a phishing website. This website is skillfully designed to resemble a trustworthy entity, be it a well-known corporation, a financial institution, or a popular online service. The goal is to create a façade of legitimacy that lulls the user into a false sense of security.
2. Strategic Deployment of the Malicious QR Code
The next step involves strategically placing these deceptive QR codes where potential victims will likely scan them. This could be in public places, like posters or flyers, or digitally, through emails and social media platforms or emails. The attackers might also hijack legitimate advertising campaigns, replacing authentic QR codes with their malicious counterparts. The placement is carefully chosen to maximize exposure and increase the likelihood of engagement from unsuspecting individuals. See the example Quishing email below:
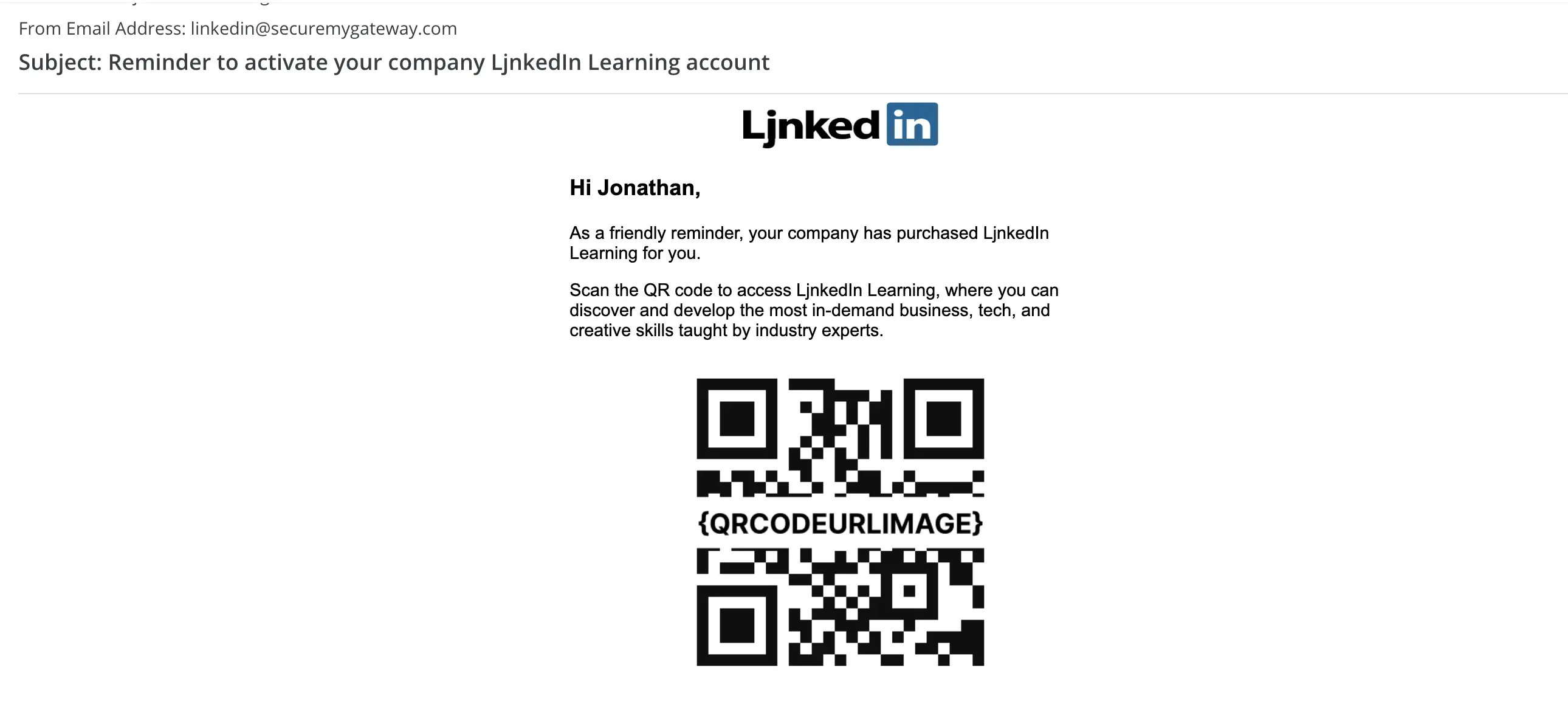
3. Execution of the Attack
Once individuals scan the malicious QR code with their smartphone, they are redirected to the phishing site. They are prompted to enter sensitive information, such as login credentials, personal data, or financial details. The user, believing they are interacting with a legitimate site, may unwittingly provide the attackers with valuable data. This information can be used for various nefarious purposes, including identity theft, financial fraud, or further cyber attacks. See the example below; once users scan the fake QR codes above, they are redirected to a fake LinkedIn page.
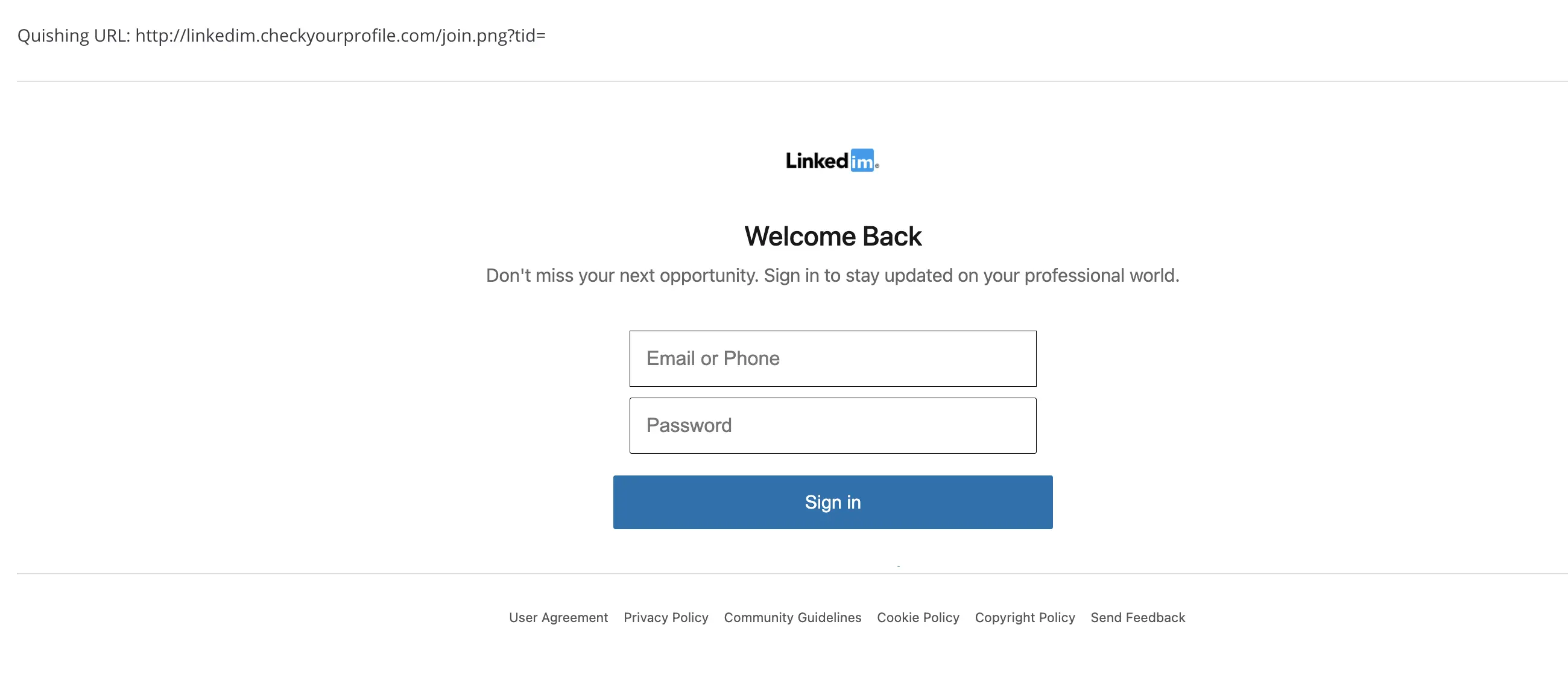
4. The Aftermath: Data Exploitation and Spread
After successfully harvesting data from victims, attackers can exploit this information in multiple ways. They might access bank accounts, sell personal data on the dark web, or use the credentials to breach other secure systems. Additionally, the attackers may use the compromised data to launch secondary attacks, either on the victim’s contacts or by using their identity to perpetrate further scams.
QR Code Phishing Statistical Overview: Quishing Statistics, Facts and Figures
This section presents a statistical analysis of Quishing attacks, highlighting their frequency, success rate, and the most affected sectors. This provides a clear picture of the current landscape, emphasizing the urgency and relevance of QR code security in today's digital ecosystem.
- Between June and August 2023, some monitoring systems identified 8,878 phishing emails incorporating QR codes, marking a concerning trend in cybercrime tactics.
- Alarmingly, recipients correctly identified and reported only 36% of these Quishing attacks, highlighting a significant gap in awareness and preparedness against such threats. This exposes many individuals and organizations to the potential dangers of these deceptive QR codes.
- Quishing campaigns more heavily target certain industries. Approximately 29% of over 1,000 malware-laden QR code emails were directed at the Energy sector, making it the most frequently targeted industry.
- The Manufacturing, Insurance, Technology, and Financial Services sectors followed closely, receiving 15%, 9%, 7%, and 6% of the malicious campaign traffic, respectively. This targeted approach by cybercriminals indicates a strategic selection of industries perceived as more vulnerable or lucrative.
- 26% of all phishing links utilized in these campaigns were embedded in QR codes, signifying attackers' substantial reliance on this method.
- In 2023, a staggering 587% increase in Quishing incidents was observed, a testament to its growing popularity among cybercriminals.
- Furthermore, 22% of all phishing attacks during in 2022 period employed QR codes, underscoring the significant role these codes play in the current phishing landscape.
- By 2025, worldwide expenditures via QR code payments will be projected to surpass $3 trillion, marking a significant increase from $2.4 trillion in 2022.
- These QR code phishing statistics highlight the escalating threat of Quishing and the urgent need for enhanced QR code security measures. As cybercriminals refine their tactics, it becomes increasingly crucial for individuals and organizations to stay informed and adopt proactive strategies to combat these sophisticated attacks. The rising trend of Quishing is a stark reminder of the dynamic and persistent nature of cyber threats in our digital world.
Identifying QR Code Phishing Attacks
Spotting Warning Signs
To spot a Quishing attack, consider the context in which you find the QR code. Be cautious if you see a QR code in an unexpected email, a random flyer, or an unsolicited text message. Reputable companies usually use QR codes in secure and predictable ways. A QR code that looks out of place or lacks clear, reliable information should be treated with suspicion.
Checking Before Scanning
Always verify the origin of a QR code before scanning it. If it's in a public area, think about whether it's appropriately placed or seems randomly added. If it's online, assess the trustworthiness of the sender. Be extra careful with QR codes that offer special deals, urgent alerts, or instant rewards – these are tactics used by attackers to rush you into action without thinking.
Real-World Examples of QR Code Phishing Attacks
In this section, we explore actual cases of QR code phishing. Through these real-life examples, we aim to shed light on the complexity and seriousness of these cyber threats. These case studies provide valuable insights into how Quishing operates, serving as a warning for both businesses and individuals.
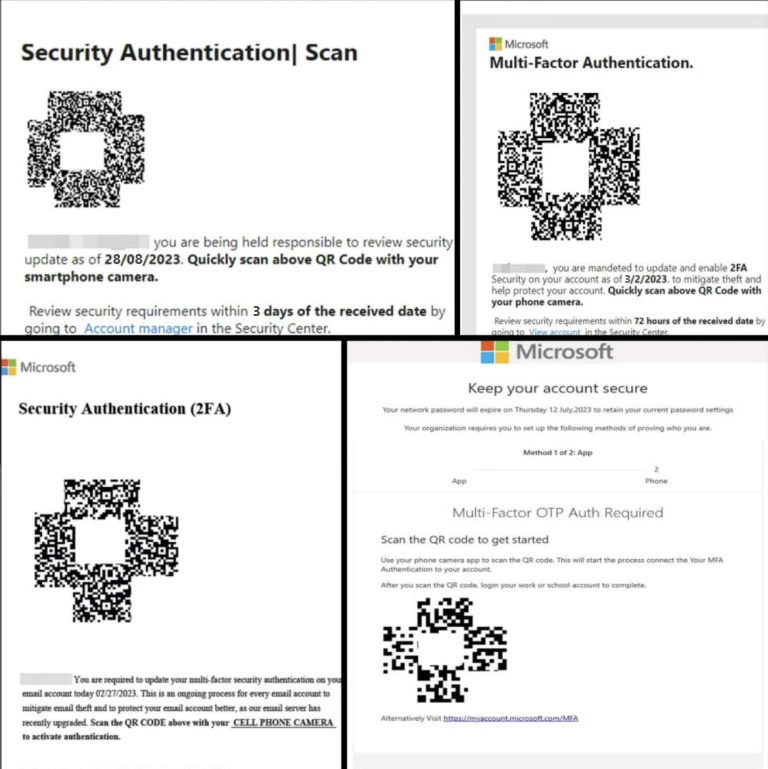
The Energy Sector Under Siege: A QR Code Phishing Campaign
One notable Quishing incident involved a significant attack on a leading U.S. energy company, signaling a new level of cyber threat sophistication. In this campaign, which affected about 29% of 1,000 examined malicious emails, attackers ingeniously used QR codes to bypass standard email security protocols. They embedded these QR codes in email attachments, deceiving recipients into scanning them under the guise of updating their Microsoft 365 account settings. This example clearly warns about the vulnerabilities present even in highly secure industries and highlights the creative tactics cybercriminals use to exploit these gaps.
Consumer Fraud: The Singapore Boba Tea Quishing Incident
In a case highlighting the risks to everyday consumers, an elderly woman in Singapore fell prey to a Quishing scam, resulting in a loss of $20,000. This scam began with a QR code affixed to a boba tea cup. The code, when scanned, directed the woman to a website that appeared to be a survey offering a free drink. However, this site was malicious and succeeded in extracting her banking details. This incident vividly illustrates the dangerous reach of Quishing in daily life and emphasizes the critical need for consumer vigilance. It is a stark reminder of the importance of being cautious and examining QR codes, even in innocuous situations.
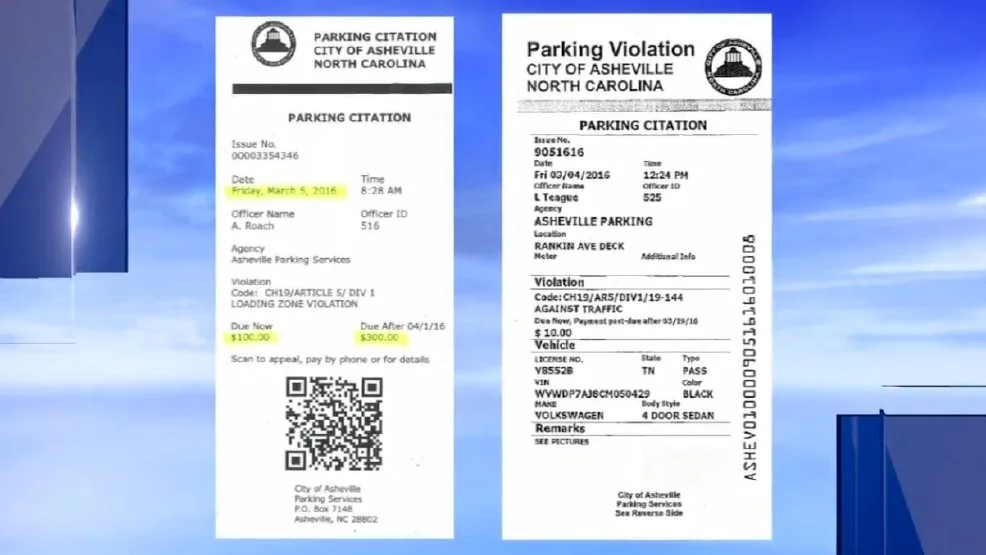
Fake Parking Tickets and Phishing in the U.S. and U.K.
Scammers in the U.S. and U.K. have exploited QR codes in fake parking tickets and fraudulent websites. In San Francisco and Texas, drivers encountered bogus parking citations with QR codes leading to scam websites. Similarly, in the U.K., QR codes on parking meters directed users to fake payment sites. These cases illustrate scammers' creative methods to target unsuspecting victims in public spaces.
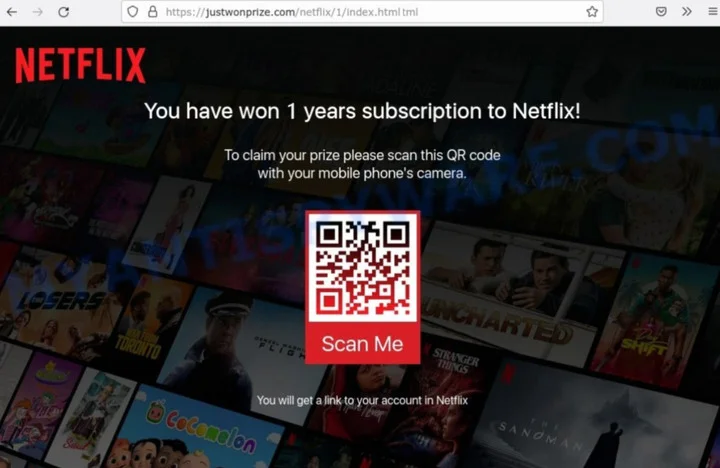
The Netflix QR Code Deception
Recently, a deceptive QR code scam surfaced, falsely promising a "2-year Netflix subscription" as bait. This scam cleverly employs QR codes as a lure and a tool for extracting personal and financial information from unsuspecting individuals. The scammers skillfully mimic official Netflix branding, including its logo, to give legitimacy to their fraudulent scheme. It's crucial to understand that Netflix is not associated with this scam, highlighting the sophisticated tactics cybercriminals use to exploit popular brands for malicious purposes.
These case studies underscore the critical need for heightened security measures and increased awareness of Quishing or QR Code phishing attacks. Businesses and individuals must be vigilant in their digital interactions, especially with QR codes. Regular training, updated security protocols, and a culture of cybersecurity awareness are essential in combating these evolving digital threats.
Protecting Against Quishing
Best Practices for QR Code Safety
The first line of defense against Quishing lies in adopting vigilant and informed practices, encouraging users to cultivate a cyber-secure culture. Individuals and organizations must prioritize QR code safety to mitigate the risks associated with these deceptive tactics. Key practices include:
- Source Verification: Always verify the authenticity of the QR code's source. Be wary of codes from unknown or unverified origins, especially in unsolicited emails or public spaces.
- Secure QR Code Generators and Scanners: Utilize QR code generators and scanners known for their security features. These tools should be able to detect and alert users of any suspicious links embedded within the QR codes.
- Educate and Inform: Regularly update yourself and your team on the latest Quishing tactics. Awareness is a powerful tool in recognizing and avoiding potential threats.
Technological Solutions: Tools and Software to Combat Quishing
Technology is crucial in combating Quishing. Various tools and software have been developed to effectively identify and neutralize these threats. Keepnet Labs' Quishing Simulator stands out as a pioneering solution. Key technological solutions include:
- Secure QR Code Scanners: These scanners come equipped with safety checks that analyze the content of QR codes before accessing the links, ensuring that users are not redirected to malicious websites.
- Advanced Threat Detection Software: Implementing software that detects and alerts users about potential Quishing attacks is vital. This software should be capable of real-time monitoring and quick response to emerging threats.
- Keepnet Labs' Quishing Simulator: This innovative tool simulates real-world Quishing scenarios, providing a safe environment for users to understand and learn how to respond to such attacks. It's an invaluable asset for training and enhancing Quishing awareness of employees.
Cultivating a Culture of Cybersecurity Awareness
The final aspect of protecting against Quishing is cultivating a robust cybersecurity culture within organizations. This involves:
- Regular Training Sessions: Conducting frequent training sessions helps keep employees informed about the latest Quishing tactics and preventive measures.
- Simulated Quishing Attack Campaigns: Using tools like Keepnet Labs' Quishing Simulator, organizations can run simulated attacks to test and improve their team's readiness against real-world Quishing threats.
- Comprehensive Cybersecurity Policies: Establishing and enforcing clear cybersecurity policies ensures that everyone in the organization understands their role in maintaining security and the procedures to follow during a Quishing attack.
- Reduce Risk: Through bite-sized content, mitigate user risk and go beyond compliance to create a cyber-resilient workforce.
- Maximize Engagement: Deploy training via email or SMS at any time, any place, on any device without the need to log in.
- Keep Training Fresh: Choose from 10 out of the top 15 awareness content providers. Find the style that works for you from 2000+ pieces of content.
- Behaviour-Based Training: Utilize innovative phishing simulators for Voice, SMS, QR Codes, Callback and MFA to deploy training based on user behavior
Protecting against Quishing requires a combination of informed practices, advanced technological tools, and building a strong culture of cybersecurity awareness. By integrating these elements, individuals and organizations can significantly reduce their vulnerability to these insidious attacks. Keepnet Labs' Quishing Simulator emerges as a key player in this arena, offering an effective platform for training and preparedness against the growing threat of Quishing.
The Benefit of Using Keepnet Quishing Simulator
- Financial Savings: Cut down on potential financial losses, which can average over $2 million, and achieve an average ROI of $89,500 through improved efficiencies and cost savings.
- Strengthened Security Measures: Pinpoint and improve risky security behaviors to build a stronger security culture, which is crucial in combating ongoing QR Code phishing attacks.
- Boost in Cybersecurity Awareness: Benefit from an 87% increase in your employees' skills to spot and report QR Code phishing attacks within three months, thanks to our targeted security awareness training.
- Legal Risk Reduction and Compliance: Avoid hefty fines and legal complications by following data protection laws.
- Regulatory Adherence: Ensure your business aligns with GDPR, CCPA, and other key regulations.
Next Steps: Protect Yourself from Quishing Attacks - Book Your Free Demo Now!
We invite you to experience our cutting-edge Quishing Simulator. This isn't just any demo – it's your first step towards robust digital protection. You can expect:
- Real-World Scenarios: Engage with simulations that mimic the latest quishing techniques. Understand how these attacks happen in a controlled, safe environment.
- Interactive Learning: Our QR Code phishing simulator isn't just a tool; it's an educational journey. Learn how to identify and respond to quishing attempts.
- Expert Insights: Get tips and strategies from our cybersecurity experts. They'll guide you through the best practices to safeguard your digital presence.
- No Obligations, Just Empowerment: This demo is completely free. We're committed to raising awareness and enhancing cybersecurity for everyone.
